Challenge: Santa’s elves have found the following image with a secret message. Can you find it?
So we get a SVG. Typical CTFs are that theres something hidden in there.

Lets first open it in a browser an look at the structure. Immediately we can see a rendering error:
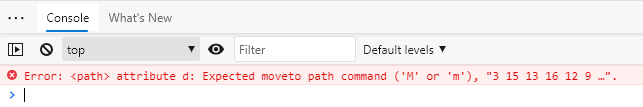
<path id="11 5 25" fill="#3C0100" stroke="#3C0100" d="3 15 13 16 12 9 3 1 20 5 4 5 14 3 18 25 16 20 9 15 14 11 5 25"/>
Hum. Numbers up to 25, it could be a letter to number cypher. Let’s try our favorite tool.
We get a response right away:
COMPLICATEDENCRYPTIONKEY.
But this isn’t the flag.
There was a lot of team effort, but this flag was not solved without the help of the organizers.
Somebody found the (original image)[stana-claus-orig.svg].
Formatting and diffing that and the one we got show small small differences in path data:
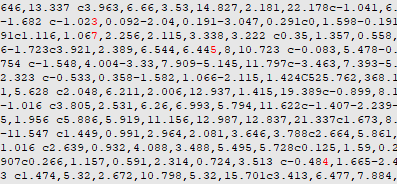
At this point I searched around for a tool and with some help did find https://github.com/japplebaum/svgsteg but running that did not produce any results.
Eventually the organizers gave the (script)[svgsteg.py] that can decrypt the massage.
$ python3 svgsteg.py -extract santa-claus.svg complicatedencryptionkey
xmas{wa1k1ng_In_a_Wint3r_w0nder1and}
It was that public svgsteg ported to python3. However the original script did not produce the same result. I have not looked why, but python2 and python3 handle something differently inside…
Flag: xmas{wa1k1ng_In_a_Wint3r_w0nder1and}
What did I learn: Ask for help, mistakes can happen.





