Challenge: Somebody sent Santa the following program and this key: thisIsMyChristmasWish. Can you help Santa find the right way to use this key and find out what the wish is?
This was a tough one, and got quite a few “angry” comments.
The contents of the JS file is a obfuscated mess. After pretty-ing the code and trying to run it in a browser - that resulted in a unresponsive page - it was time to dig into the code.
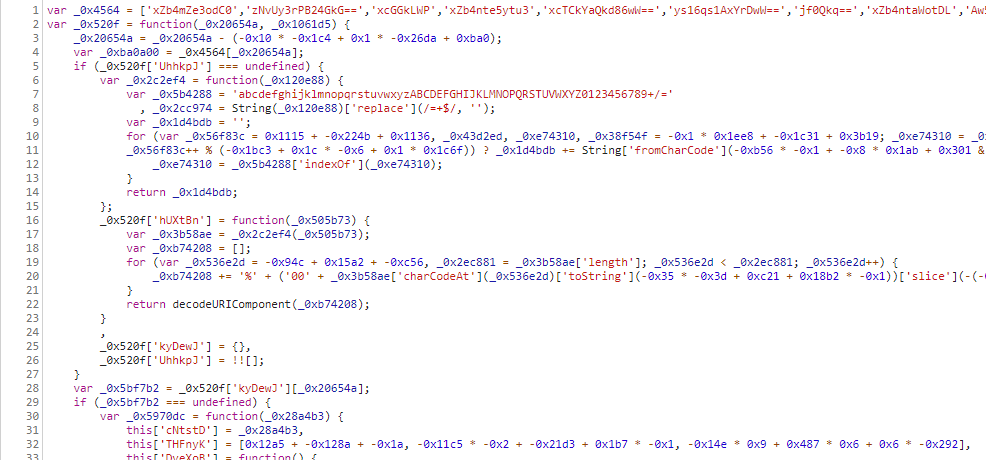
First we try to figure out, where the code gets stuck, whats run by default. The first part of code is some sort of decoder and execution gets stuck there. We comment out some lines:
// new _0x5970dc(_0x520f)['RaKowv']()
And below a timer that calls a function, we’ll comment out that setInterval too.
After going over a bunch of functions, carefully commenting out intentional forever-loops and avoiding dead code, we end up with a bunch of texts:
_0x30dc23()Cobra, Bear, Tiger, Alpaca_0x52a41d()Alligator, Ant, Elephant, Baboon_0x396381()Drum fish, Jellyfish, Blowfish, Angel fish_0x371e09()Black Bear, Bat, Beetle, Chicken_0x178dde()moAcw9dmeJjsSCAuwaQt2nyU5hiUnQxM7JhAItdkBCq9gew3bgGL7w==
There were more functions, larger ones, with crazy state machine-like components, but led nowhere…
Here’s the cleaned up version: present_fxed.js.
Ok, but now what. Animals are fine, but what is that base64 looking text? At the start of the code, we have a decoder that works with strings that look like b64, but are actually now. Is it the same here? And what to do with it?
Friends pointed out, that it’s obviously encryption and one of the animals is the clue. I know of Blowfish since way back, first time I encountered it was with Eggdrop (IRC bot).
Here is where I made the mistake and used the wrong tool that led me to spin in circles. I tried to use https://gchq.github.io/CyberChef to bake the correct Blowfish decryption , but I could not manage to prepare the key the right way. Eventually I tried http://sladex.org/blowfish.js/ and was able to decode it with default parameters (ECB).
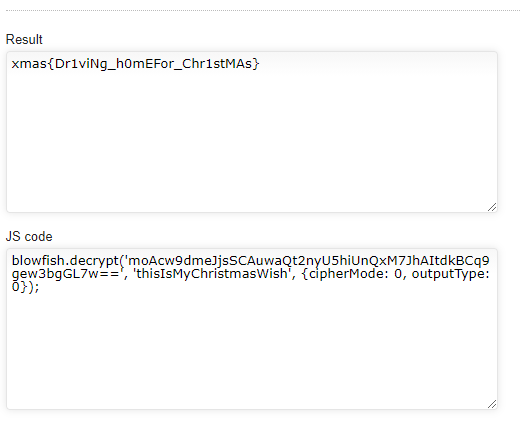
This flag was very frustrating, and had a lot of guessing elements…
Flag: xmas{Dr1viNg_h0mEFor_Chr1stMAs}
What did I learn: I hate javascript, and try more than one tool for decryption.





