Challenge:
Santa forgot his password from last year for the gift system, all he has is the password hash from the backup database - 0e05910310684507431798973709823129745294. The password is too strong to crack even for his magic mining rigs. His elves are not very good web developers though so it shouldn’t be hard to find a way to log into the app.
https://blitzen.bsidesljubljana.si/
A green page with one input field pops up…
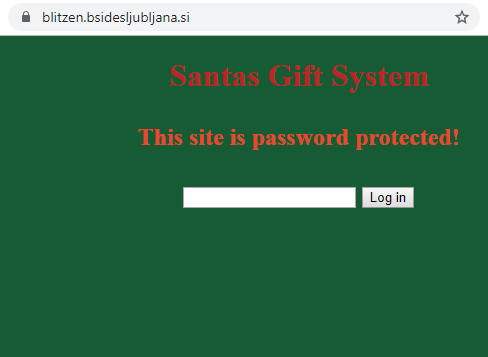
Could it be SQL injection?
’ or 1=1 –
That didn’t work… Whats this 0e… thing? And the site is PHP?
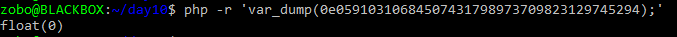
Oh, I remember… It’s the PHP operator == that does type conversion… It converts the string of 0e05… into float 0, since is the exponent float notation it basically says 0 * 10^059… = 0.
By looking at the length of this “has” we can deduce its a SHA1 operation, so we can guess there is some code like this below:
if (sha1($_GET['password']) == "0e05910310684507431798973709823129745294") {...
The obvious solution is, find a password that will hash into 0e… something. This will then evaluate to true, like this:
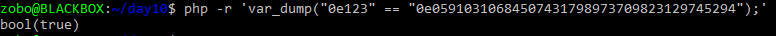
So the task remains, what kind of input to SHA1 will produce a 0e… string? Turns out this is also a solved problem.
Enter 10932435112 and we get…
Flag: xmas{L4sTXm4$iG4vEy0uMyFl4g}
What did I learn: Well, PHP is a dabgerous language… So, nothing new.





