Challenge: The naughty and nice list must always be kept safe. That’s why Santa password protected the document and stored the encrypted password in this app. Can you get the password out for him?
The attached file was App.apk.
Obviously Android. So I first went to decompile it to do some static analysis. I first used apktool, but while the tool got me raw xml files, it did not produce java or class files of the code but rather smali. So I went for an online tool again, http://www.javadecompilers.com/ that offered a nice download of decompiled java files along with everything else.
Digging a bit around you get to these two parts:
String encb64 = new String(Base64.encode(C0559a.m2510a(this.f1953b.getText().toString(), MainActivity.this.getString(R.string.key), MainActivity.this.getString(R.string.iv)), 0)).replace("\n", "");
Log.d(MainActivity.f1952p, String.format("enc b64 => %s", new Object[]{encb64}));
if (encb64.equals(this.f1954c)) {
Toast.makeText(MainActivity.this, "Correct", 0).show();
} else {
Toast.makeText(MainActivity.this, "Try again", 0).show();
}
public class C0559a {
/* renamed from: a */
public static byte[] m2510a(String data, String k, String i) {
byte[] key = Base64.decode(k, 0);
byte[] iv = Base64.decode(i, 0);
SecretKey secretKey = new SecretKeySpec(key, "AES");
Cipher cipher = Cipher.getInstance("AES/GCM/NoPadding");
cipher.init(1, secretKey, new GCMParameterSpec(128, iv));
return cipher.doFinal(data.getBytes());
}
}
After getting to know a bit the variables, you can see what is going on here. The input field is encrypted and then compared to the stored encrypted flag. All values are in the strings.xml
Better than before, but since AES is symmetric cryptography and we have the key and IV it’s jut a question to turn the code a bit around so that I can pass in the the B64 encoded flag.
text = AES(AES(text))
flag=/8HY8EuHfq0boYvy8C4x7vMKbWnYgk8svF8x4ksMoqT/f1nBcv976MuZn1nOyQ==
key=gUyEkkZOThLD/Hl9Op4Spw==
iv=c5oemnr8p2ocw6H7
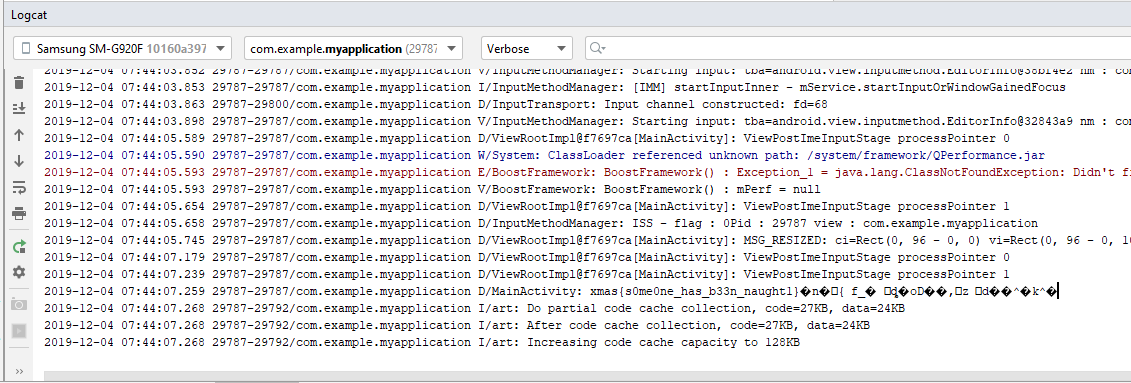
In the end I used one of my devices to bang the code together and print out the decrypted key.
Flag: xmas{s0me0ne_has_b33n_naught1}
What did I learn: Symmetric cryptography is… symmetric.





