Challenge: Santa forgot his password for the application he likes to use, but he found this old binary that contains the password. Can you help him retrieve it?
This was a reversing challenge. The binary took a string and it told you if it was valid. Sort of like a serial checker. To solve this one one had to calculate each step of the way what the input parameters might be or one could help himself with z3.
First we need to find the function. Ghidra had some problems, so I captured the call to sscanf with GDB, made a core dump and loaded that. Alternatively I could have done it statically one I knew where to look for.
The reversed function looked like this.
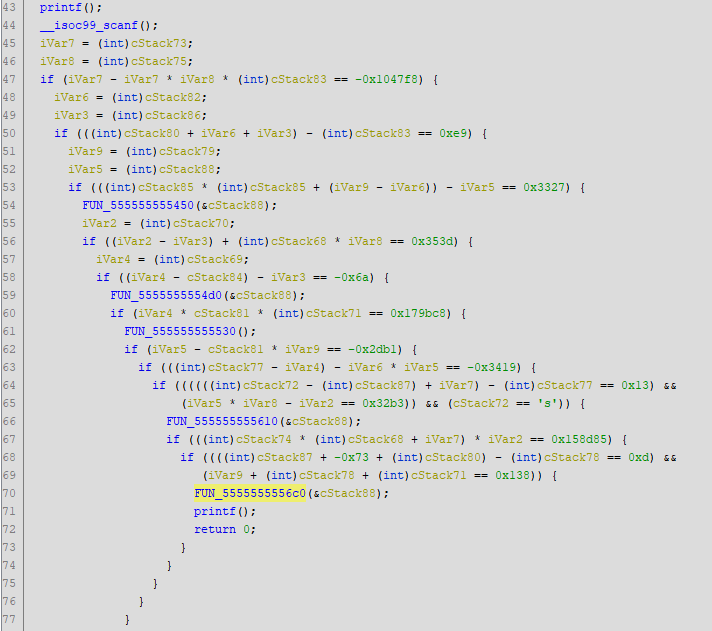
Calculating something like this by hand (there are 21 characters!) would have been a real pain, so I took a look at Z3, as suggested by one of the players.
There, you describe constraints and then the library (the solver) gives you a possible input.
To avoid making a mistake, I tried to follow the code generated by Ghidra as close as possible. Indeed there was a small catch, where one of the bytes was not process by the main function but rather by one of the other ones.
The whole code is here: test.py
And the result.
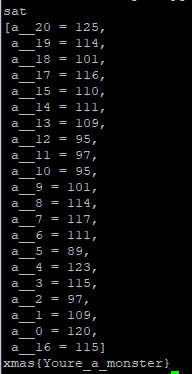
Flag: xmas{Youre_a_monster}
What did I learn: To use Z3.





