Challenge: Isn’t 2fa fun? Especially when you forget to backup you code and can’t login anywhere anymore. Well, not even Santa is immune to mistakes like this. Fortunately his app creates a recovery token. The developers hoped that Santa would never need it, so they kinda slacked off when implementing the app. It’s up to us to find Santa’s recovery token.
Android! This was a perfect opportunity to try out a new VSCode plugin, APKLab. With a few JAVA_HOME quirks I got it up and running and decompiled the APK.
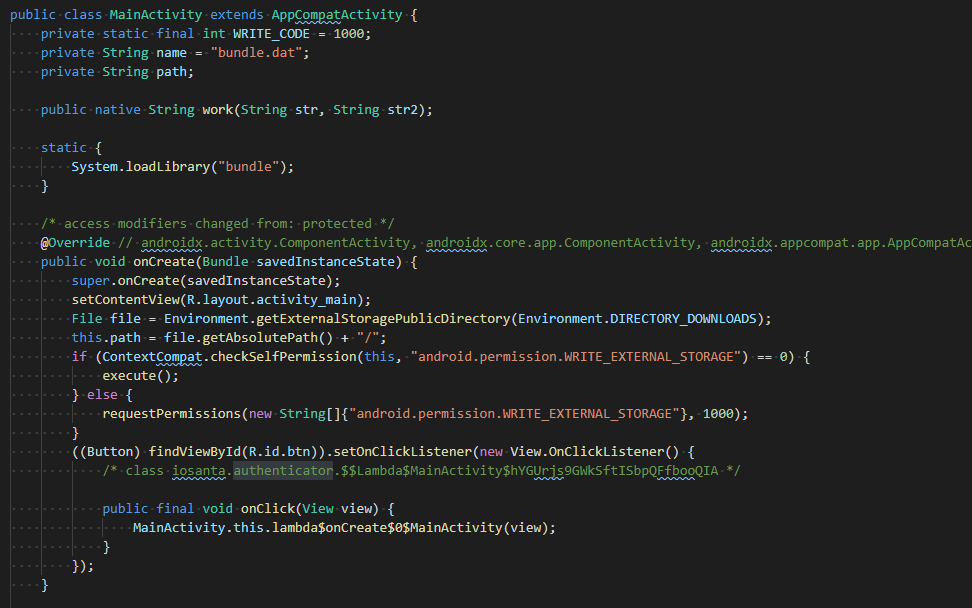
Ok, so obviously less Android and more Native. There is a libbundle.so that we need to inspect.
Altho nothing much useful, there was one function that jumped out:
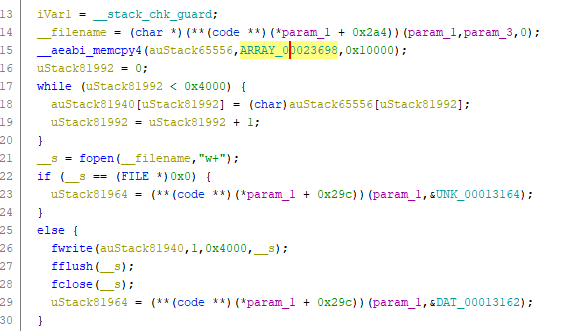
It does some memory copy and write to file. Could be a “recovery token”.
The start of the array looks like a SQLite database, also there is some “garbage”. Scrolling over the array reveals the flag:
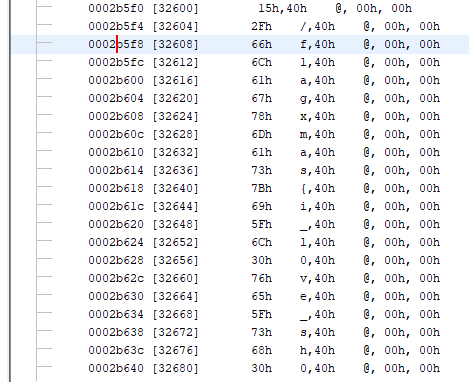
As it seems only every forth byte is “valid” I made a quick “cut” script that will just output every forth byte. Passing it through strings…
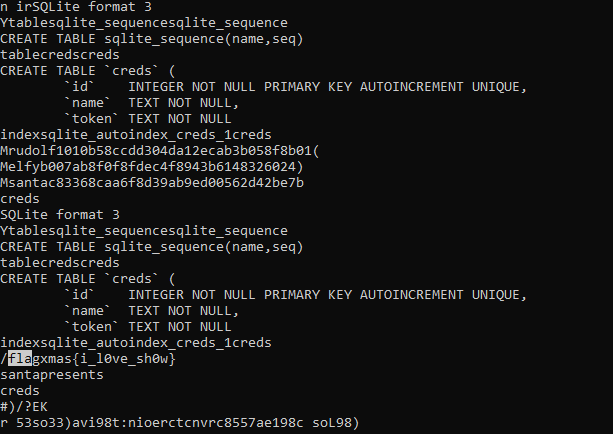
Perhaps the idea was to actually extract SQLite database and then inspect it, but this also works.
Flag: xmas{i_l0ve_sh0w}
What did I learn: Learned to use APKLab.





